Some Known Facts About Webintegrity.
Wiki Article
The Facts About Webintegrity Uncovered
Table of ContentsWebintegrity Fundamentals ExplainedThe Single Strategy To Use For WebintegrityWhat Does Webintegrity Mean?
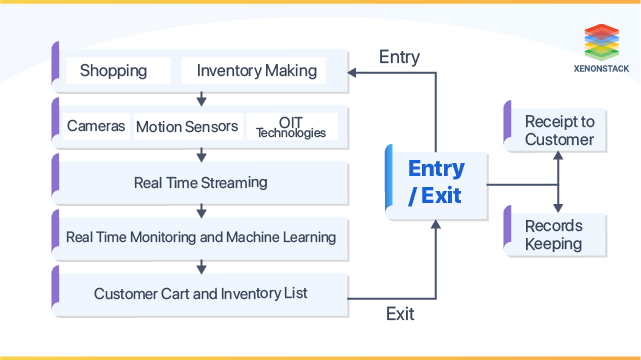
If you run a shopping company, you'll desire
to optimize your enhance to web servers issues like downtime, bandwidth overload data transfer long loading timesFilling Checking your network in real time can reveal workable understandings about problems as well as performance inadequacies that require to be attended to."Not only do business leaders obtain to recognize the status of their network performance as well as safety and security at all times, but when a case happens, the real-time notifying allows for faster incident reaction, "said Pieter Van, Iperen, creator and managing companion of PWV Professionals.
The 9-Second Trick For Webintegrity
It is vital for businesses to solve occurrences as soon as they emerge, nonetheless large or little they appear to be." When performance modifications or there is a safety and security alert, the system can inform you to make sure that repairs can be executed. This is why it is key to know what is regular for the business without understanding what is normal, company leaders have no idea how to set signals (https://www.avitop.com/cs/members/webintegrit.aspx)."There are several keeping track of applications on the marketplace, which range in attributes, technical competence and also cost."I suggest choosing a service that is easy to apply as well as use. If you need more complex devices in the future, you can update. There is a device to fit every circumstance.". By keeping track of operational tasks such as supply levels or item usage patterns, it becomes simpler for managers at any type of level to determine which processes requirement renovation or optimization.
You can conserve time and resources by executing new ones without very first checking if those enhancements will really lead to price financial savings with time. Due to the nature of the BAM, managers can react to these exceptions proactively as they can make use of real-time information. Cflow's BAM can be made use of to observe all your process-relevant activities that happen across your company (https://www.sbnation.com/users/webintegrit). You can incorporate activity details as well as commute metrics and also apply organization rules to set thresholds for very easy visualization of the kept an eye on data.
Company Refine Measurement(BPM )is a means to keep an eye on as well as gauge organization processes, which can be utilized for: Gauging the performance of a process or process improvement. Automating organization procedures. A product instance is an organization object that has actually been instantiated in your system. It stands for the smallest device of company process surveillance, which can be used to keep track of private instances of an item by utilizing its distinct identifier (ID). Using just one KPI might not properly reflect the real state of either process. Making use of multiple KPI metrics helps guarantee that monitoring has accessibility to pertinent info at all times throughout their daily operations. An essential performance indicator( KPI )is a dimension of progress towards the success of a specific goal. One of the most usual kinds of KPIs consist of: Earnings targets Roi( ROI) metrics Earnings margin portions Metricsare a way to determine as well as keep track of the performance of a company. Metrics are certain to the service and also must be defined prior to beginning any BAM project. It is very important that metrics be specified by the organization users, not IT or advertising experts. g., when an email was sent out successfully image source but there was no recipient address stored for that individual,this would cause the trigger to discharge off an alert about "no recipients". A debug log is created after each event has occurred. This assists you know what happened during that time period without requiring any type of extra details from individuals who logged right into their accounts throughout those moments. Without the debug log, it will certainly end up being difficult to recover the lost information as well as to maintain track of the modifications that happened in between the events.
Report this wiki page